Securing the Web: Understanding SSL/TLS, Cryptography, and Different Certificate Types
Unmasking the Magic Behind Secure Online Communication
Table of contents
The internet has become the lifeblood of our modern world, woven into the fabric of our daily activities. From online banking that keeps our finances afloat to social media that connects us across continents, it transmits a constant stream of sensitive information. But how can we be certain this information reaches its intended destination without prying eyes or malicious tampering? This is where SSL and its successor, TLS, step onto the stage as the guardians of online security.
SSL, or Secure Sockets Layer, and TLS, or Transport Layer Security, are the cornerstones of secure communication on the web. Though SSL paved the way, TLS is its more robust and widely adopted descendant. Both protocols leverage the power of cryptography, the art of transforming messages into unreadable code, to achieve three critical security objectives:
Confidentiality: Imagine a conversation whispered in a crowded room, only audible to the intended recipient. That's the essence of confidentiality. TLS ensures that only authorized parties can access the data being transmitted, keeping it safe from eavesdroppers and data snoops.
Integrity: Have you ever received a garbled text message, its meaning twisted beyond recognition? Data integrity ensures the information you send arrives at its destination exactly as you sent it, without any alterations or manipulations during transmission.
Authentication: In an online world teeming with imposters, authentication verifies the identities of the parties involved in the communication. Just like checking someone's ID before granting entry, TLS ensures you're truly communicating with the website you intended to visit, not a cleverly disguised imposter.
Why TLS Matters: Protecting Our Digital Lifeline
In today's digital age, where sensitive data flows freely across the web, robust security measures are no longer a luxury, but a necessity. TLS safeguards a vast array of information, including:
The credit card details you enter during online purchases, ensuring they reach the merchant securely.
The private messages you exchange with loved ones, keeping your conversations confidential.
Your login credentials on websites, protecting your accounts from unauthorized access.
The data exchanged in various applications like instant messaging and video conferencing, guaranteeing the privacy of your communications.
By encrypting communication channels, TLS acts as an invisible shield, deterring eavesdroppers and data tampering. The small padlock icon you see in your browser's address bar for secure websites (HTTPS) signifies an active TLS connection, a silent guardian working behind the scenes.
Under the Hood of TLS: The Handshake – A Secure Ballet
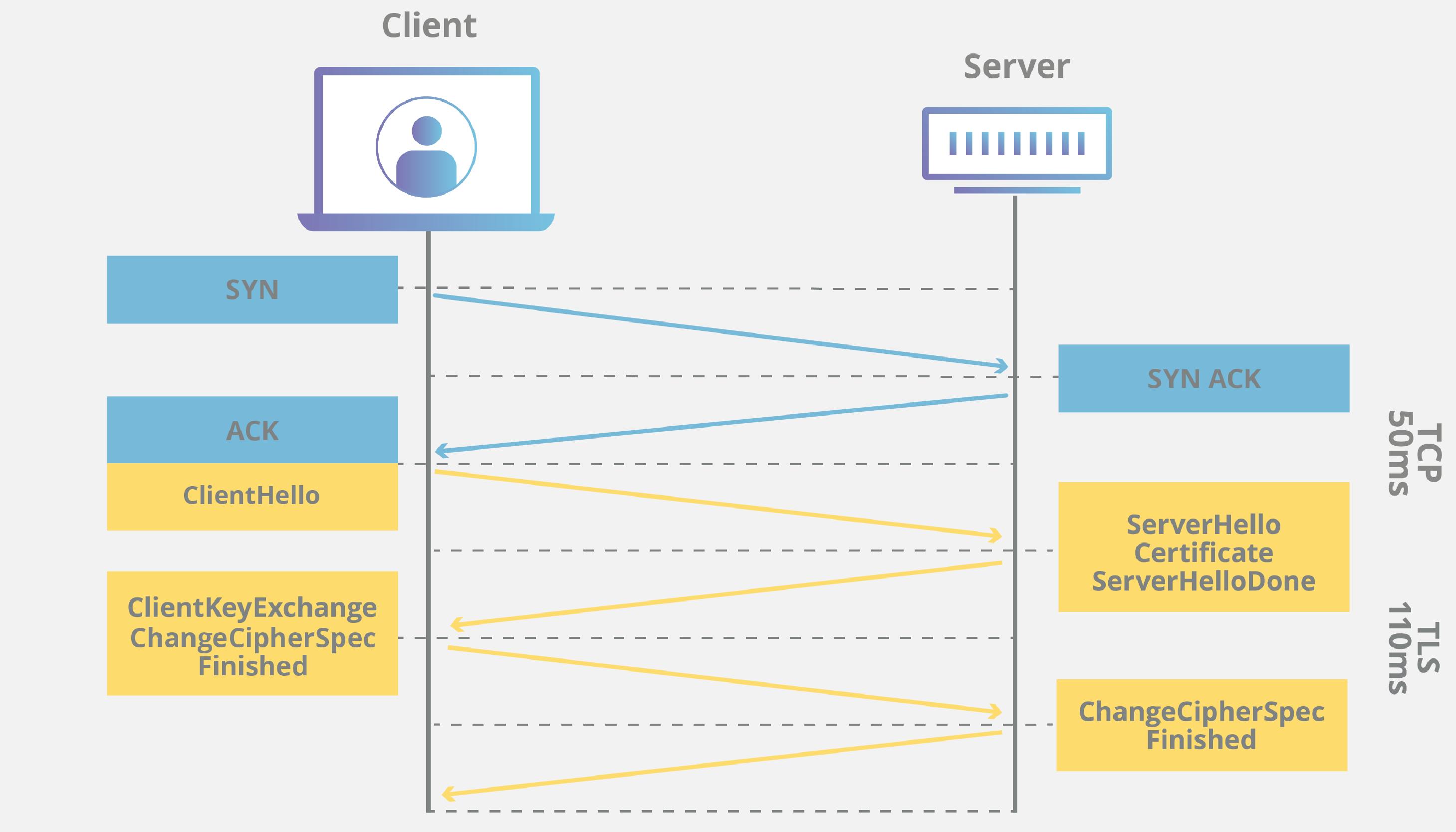
TLS establishes a secure connection through a meticulous process called the handshake. Imagine two dancers performing a carefully choreographed ballet to establish trust and communication. Here's a simplified breakdown of this cryptographic dance:
Initiation: The client (your browser) initiates the dance by requesting a secure connection from the server (the website).
Cipher Suite Negotiation: Like two dancers agreeing on the music and steps, both parties negotiate on the encryption algorithms and digital certificate to be used for the secure communication.
Server Authentication: The server presents its digital certificate, acting as its digital ID card, for verification by the client. Just like checking identification before allowing someone on stage, the client ensures the server is who it claims to be.
Key Exchange: Public-key cryptography, a marvel of modern mathematics, comes into play here. Imagine the dancers exchanging specially coded tokens to establish a secret communication channel. TLS uses public-key cryptography to establish a secure session key for encrypting the communication.
Secure Data Transmission: Once the handshake is complete, the real communication begins. Data is encrypted with the session key, ensuring confidentiality and integrity. Just like the dancers moving in perfect sync after establishing their connection, information flows securely between the client and server.
The Balancing Act: Symmetric vs. Asymmetric Cryptography
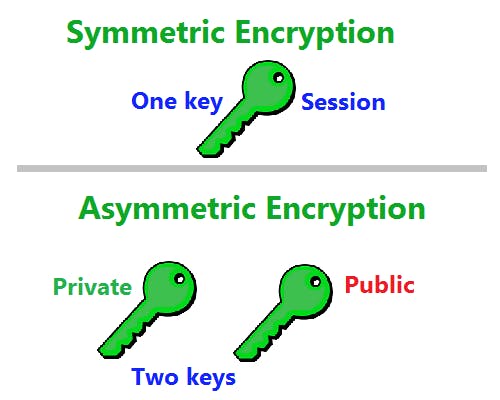
TLS employs a fascinating interplay between two cryptographic techniques:
Symmetric cryptography: Imagine two best friends sharing a secret code to write encrypted messages. Symmetric cryptography utilizes a single shared secret key for both encryption and decryption. This method is efficient but requires a secure way to establish that shared key beforehand.
Asymmetric cryptography: This technique introduces the concept of a public-key pair, like a special lock and key combination. Data encrypted with the public key (available to everyone) can only be decrypted with the corresponding private key (kept securely by the server). This is crucial for securely transmitting the session key during the handshake, where a shared secret isn't available yet.
TLS cleverly combines both techniques for optimal security. Symmetric cryptography provides speed for encrypting data during the communication phase, while asymmetric cryptography safeguards the initial exchange of the session key.
The Evolution of Security: TLS 1.2 vs. TLS 1.3
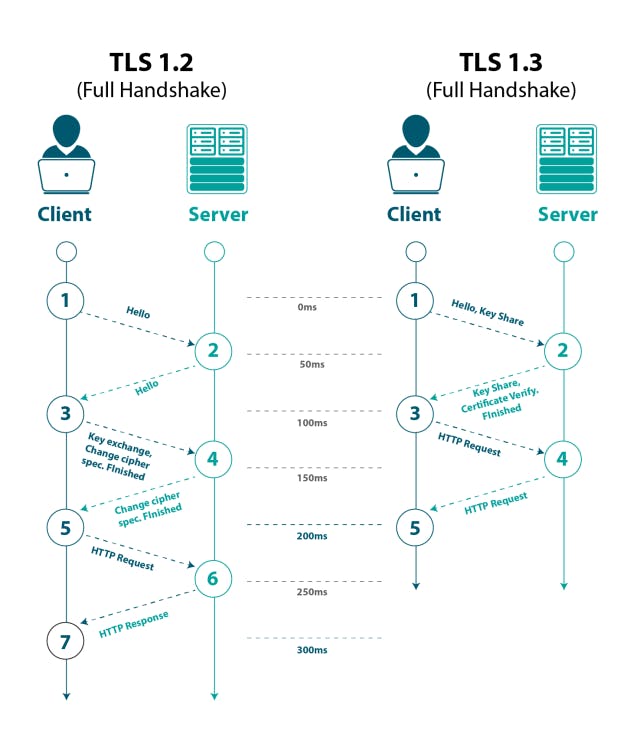
As technology advances, so do the threats lurking in the digital shadows. The world of TLS is constantly evolving to combat these emerging challenges. Here's a closer look at the two most recent versions of this vital protocol:
TLS 1.2: The current industry standard, TLS 1.2 offers robust security but has some known vulnerabilities. Think of it as a well-armored castle, offering a strong defense but with a few weaknesses that could potentially be exploited by a determined attacker.
TLS 1.3: The latest iteration, TLS 1.3, is the upgraded version of our digital castle. It boasts improved performance with faster encryption algorithms, utilizes stronger ciphers to combat known vulnerabilities, and streamlines the handshake process for quicker connection establishment. Imagine the same castle, reinforced with stronger materials, featuring more efficient defense mechanisms, and a more streamlined entry process.
The security community is actively migrating towards TLS 1.3 for its enhanced protection. Just like upgrading our security systems at home, adopting TLS 1.3 strengthens the overall security posture of the web.
Beyond the Basics: A Realm of Certificate
TLS relies on digital certificates issued by trusted Certificate Authorities (CAs) to verify server identities. These certificates act as digital passports that vouch for the legitimacy of the website you're communicating with. Different types of certificates cater to various needs:
Domain Validation (DV) Certificates: The most basic type of certificate, DV certificates simply confirm that the website owner controls the domain name. Imagine a simple ID card that verifies you are who you say you are.
Organization Validation (OV) Certificates: Offering a step up in security, OV certificates provide additional information about the organization behind the website, like its name and location. Think of an enhanced ID card that includes your address and other details for more thorough verification.
Extended Validation (EV) Certificates: The most stringent and trustworthy type, EV certificates undergo a rigorous vetting process to confirm the organization's legitimacy. These certificates display a prominent green padlock in the browser bar, offering the highest level of user trust. Imagine a government-issued passport with extensive security features, granting the website the highest level of credibility.
Understanding SSL/TLS and its underlying cryptographic mechanisms empowers you to navigate the digital world with confidence. By employing these protocols and the different certificate types, we can ensure the security and privacy of our online interactions, safeguarding the sensitive information that flows through the veins of the internet. So, the next time you see that little padlock icon in your browser bar, remember the intricate dance of cryptography and the silent guardians – TLS and its certificates – working tirelessly behind the scenes to keep your online world secure.
Advanced TLS Features and the Future Landscape
While we've explored the core functionalities of TLS, it boasts a treasure trove of additional features that further enhance online security:
Perfect Forward Secrecy (PFS): Imagine a handshake where even if an attacker intercepts the session key, they cannot decrypt past communication due to the use of ephemeral (short-lived) keys. PFS offers this very protection, adding an extra layer of defense.
Session Resumption: TLS optimizes performance by allowing previously connected clients and servers to resume sessions without a complete handshake, saving valuable time and resources.
Server Name Indication (SNI): On a web server hosting multiple websites, SNI identifies the specific website a client intends to connect to, improving security and efficiency.
The future of TLS is bright, with ongoing development focused on:
Post-Quantum Cryptography: As quantum computing evolves, it could potentially break current encryption methods. TLS is actively exploring post-quantum cryptography algorithms to stay ahead of the curve.
Standardization of TLS 1.3: While TLS 1.3 is gaining traction, wider industry adoption is crucial. Continued standardization efforts will ensure seamless integration across different platforms and browsers.
Automation and Transparency: Automating certificate management and improving certificate transparency will further streamline security practices and user trust.
Beyond the Web: The Expanding Reach of TLS
TLS isn't confined to securing web traffic. Its applications extend to various areas, including:
Virtual Private Networks (VPNs): TLS encrypts communication within VPN tunnels, safeguarding data privacy.
Email Security: Protocols like SMTPS and STARTTLS leverage TLS to encrypt email communication.
Instant Messaging: Many instant messaging applications utilize TLS to ensure the confidentiality of your messages.
As our reliance on digital communication grows, TLS will undoubtedly play an even more pivotal role in safeguarding our online interactions.

